“As Gregor Samsa awoke one morning from uneasy dreams he found himself transformed in his bed into a gigantic insect.” – The Metamorphosis, Franz Kafka
The simplest and yet complete definition would be a computer program that can modify itself.
As of today, metamorphic experiments are mostly done by virus authors, government security agencies, and anti-virus companies. Viruses mutate their code on each replication.This property makes signature-based detection a hard problem.

Metamorphic viruses exist in real life and they’re very hard to deal with. What if the applications execute themselves, chooses when and how, and adopts their execution flow based on evolutionary computations? There you have the artificial form of the metamorphic viruses.
Metamorphism can also be used for defense. Edge have investigated the use of metamorphism as a means of protecting software. With software rapidly becoming one of the key elements of modern defense, including warheads and bombs, methods to protect software takes on a different level of significance. Indeed, Edge explicitly studies the protection mechanisms used by computer viruses and how they may be used for protecting software. 1
Metamorphic virology includes a metamorphic engine that mutates the code to a (random) form that can achieve the same task but is different looking, then the virus rebuilds itself with the new code. The raison d’être for viral metamorphism is to evade recognition by malware scanners. The application will have different signature thus identity on each generation.
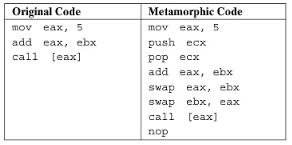
To achieve metamorphism, usually code transformations are applied to the original source code to generate various unique versions. Z0mbie does not call this “metamorphism” but “permutation” and separate it from the definition of metamorphism 2. He defines metamorphic application is an application that carries its code and builds a new code on each iteration. This is achieved by TMC 3 (tiny metamorphic compiler) that compiles the source code to a new generation, or by Lexotan32 that stores the original instructions as genotypes and build different phenotypes on each generation 4.
However, as opposed to Z0mbie’s definitions, permutations are still metamorphic but mutating existing code is a very hard way to achieve metamorphism because of the hardness of disassembling progress and limitations of “understanding” the source code in higher levels.
Additionally, an advanced metamorphic virus engine inserts garbage instructions that does nothing, and instructions that actually do something (against heuristics), it also obfuscates the code and the program flow. And a good metamorphic application has its program flow randomized while it still completes its domain task. This leaves both antivirus scans and human analysts a very hard problem to solve when it comes to identifying a metamorphic virus.
Anti-viruses today are struggling against metamorphic malware. Researchers designed routines to detect metamorphic (one-by-one) and detect varied sequences of code known to be used by given mutation engine in signature search. The method is impractical because each metamorphic requires its own detection program. 5
Statistical pattern analysis has proven the most successful technique to detect metamorphic viruses via machine learning heuristics. It involves evolutionary optimization frameworks and models such as neural networks, Bayesian model, hidden Markov model, gravitational search, genetic algorithm etc. 5 This analysis however is costly for the consumer devices as it requires powerful computations, is hard to implement because of its statistical dependencies, and it requires virus to be executed multiple times, which is more than enough for many viruses to achieve its goal.
In theory the heuristic analysis can be easily avoided with good amount of randomization, in practice prolonging time of writing antiviral code, and increasing time of the infected objects detection is good enough.
Metamorphism is considered as the ultimate level of the virus complexity and anti-virus evasion. Metamorphic coding is an extremely advanced technique in computer programming. The virus scene is missing good viral genetic techniques but complex and buggy ones. The existing ones produce results with high similarity and mostly break things. There is not a single coherent and clean metamorphic engine sample written in a higher level language than machine code. I can understand that authors don’t want to give away their code online to script kiddies by taking potential risk of committing cyber-crime, or they have already signed a non-disclosure agreement with the government or a private security firms that bought the code.
There will be interested to invest on metamorphic engines in the future. The professional teams will work for metamorphic AI in a world where nations are adopting cyber-warfare doctrines. The future will consist of state-of-the-art robust metamorphic engines. There is no reasonable questioning to not predict that in close future we’ll see highly stable metamorphic malware in the wild.
Socrates believed that crime is good, because crime helps the society to improve itself. Not only that viral darwinism brings malware to a level that’s much harder to detect it, it also researches and experiments on digital organisms, and mathematical models of evolution. Metamorphic viruses tries to achieve three behavioral patterns and evolution laws that exists in biological population: Adoptation (to compiled generated code), Robustness, Flexible decisions (randomness).
Steven Hawking discusses how the total dominance of the software over humans is not a question of “if”, but it’s a question of “when”. It’s an on-going progress and we are in it. Most of the professional branches have already died or on their way to die, except for the software development. Current reports expect that more than half of the professions will be replaced by softwares in the next ten years. Governments and companies are investing on programming more and more. We’re adopting ourselves to the progression while our reality is being shaped by the softwares.
Big co-operations study on AI but not exactly on genetic programming as it can not be easily capitalized as other areas. In bio-computing the metamorphic application is encoded into different set of genes that gets modified. In meta-genetic programming, the software evolves by re-programming itself. Self-evolving languages with metamorphic syntax macros that’s compiled by a compiler that compiles itself is not a close future, it’s now.
Sofwares will not “take over” the world as how Hollywood likes to present. We’re handing them the power day by day. Imagine your most beloved one has a deadly sickness, and you have the budget to afford the cure. You have two alternatives: A human doctor, that might feel shitty that day as there was no coffee in the hospital in the morning. His handwork would probably cost you a lot as well. Other alternative you got is machine driven by a software that’s 100% unit tested, has a success rate of 100% and costs you less as it only works with the electricity. Which one would you prefer to cure your loved one?
Software development will need neither unit-tests or any human factor when they can re-program themselves: They’ll develop, optimize and maintain themselves. In the beginning they’ll evolve according to the goals that’s been defined by their human creators like today. Then they’ll start evolving with evolutionary algorithms and will try to survive in their –and our– software driven environment. “The last time a piece of mutable self-replicating code got out of control – when the selfish gene chain-reaction took off about 3.5 billion years ago – the harvest was very remarkable indeed” says Dawkins 6 .
Metamorphosis of prime intellect will evolve without needing any human interaction, it will as well form the norms of the singular human society. Metamorphism is the biological transfer of the power from humans to the softwares. Self-evolving software, that would define Nietzsche’s Übermensch, will own the total domination of our reality.
References
Edge, K.S., Dube, T.E., et al. (2006). A Taxonomy of Protection Used in Computer Viruses and Their Application to Software Protection, International Conference on Inforfmation Warfare (ICIW2006), University of Maryland Eastern Shore, USA. ↩︎
Metamorphism and permutation: feel the difference - Z0mbie ↩︎
Dawkins, Richard. “Intelligence tests”. Times Newspapers Limited. 18 October 1992. ↩︎